Authenticity of Intent: Verify Every AI Agent Action with Confidence
Ensure every AI agent request truly reflects your users' intent. Our AP2 integration provides cryptographic proof that actions are authentic, eliminating AI hallucinations and unauthorized transactions. Build trust in the AI-powered commerce era.
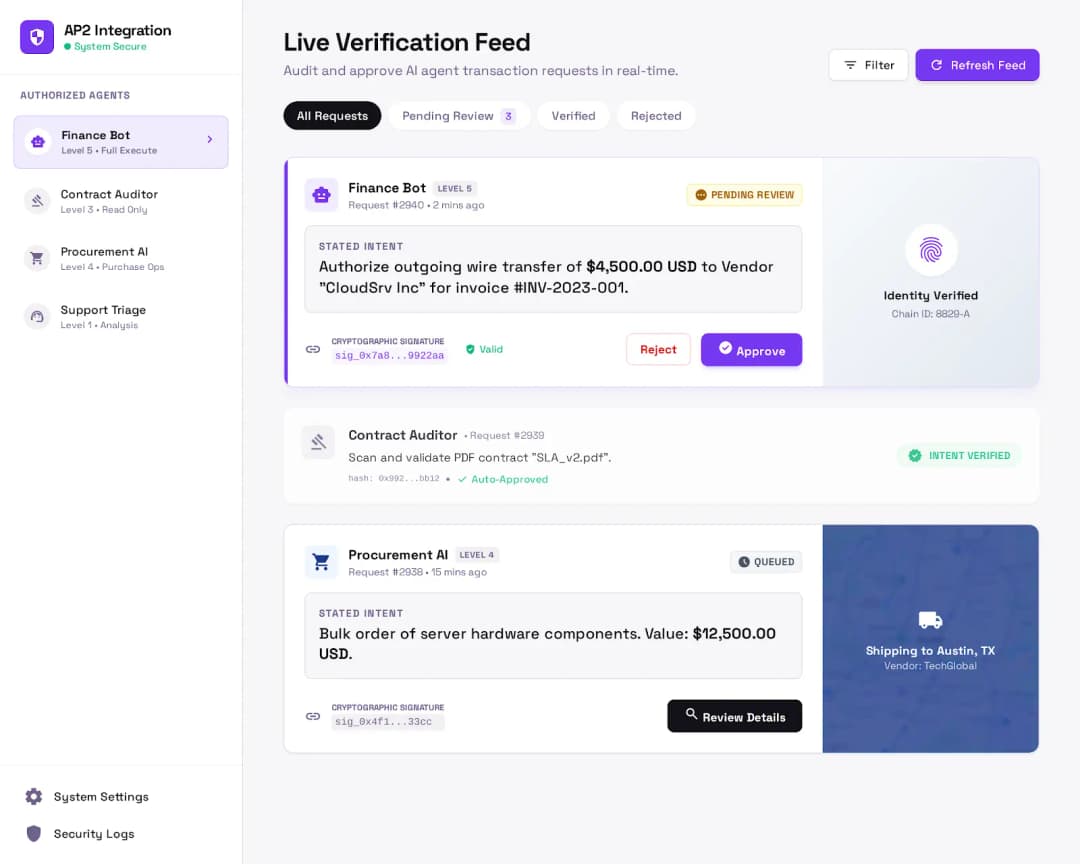
How AP2 Intent Verification Works
Our AP2 integration ensures that every action initiated by an AI agent is cryptographically verified to match the user's true intent, protecting merchants and users from AI errors and unauthorized actions.
- 1
User authorizes AI agent with verified identity
Users authenticate themselves and grant specific permissions to AI agents through our secure verification flow. Each authorization is recorded with biometric confirmation and cryptographic signatures.
- 2
Agent requests are cryptographically signed
Every action requested by the AI agent carries a cryptographic signature linking it to the user's verified identity and authorized permissions, creating an immutable chain of intent.
- 3
Merchants verify authenticity in real-time
Before processing any transaction, merchants can instantly verify that the request originates from an authorized user, matches their stated intent, and falls within permitted boundaries.
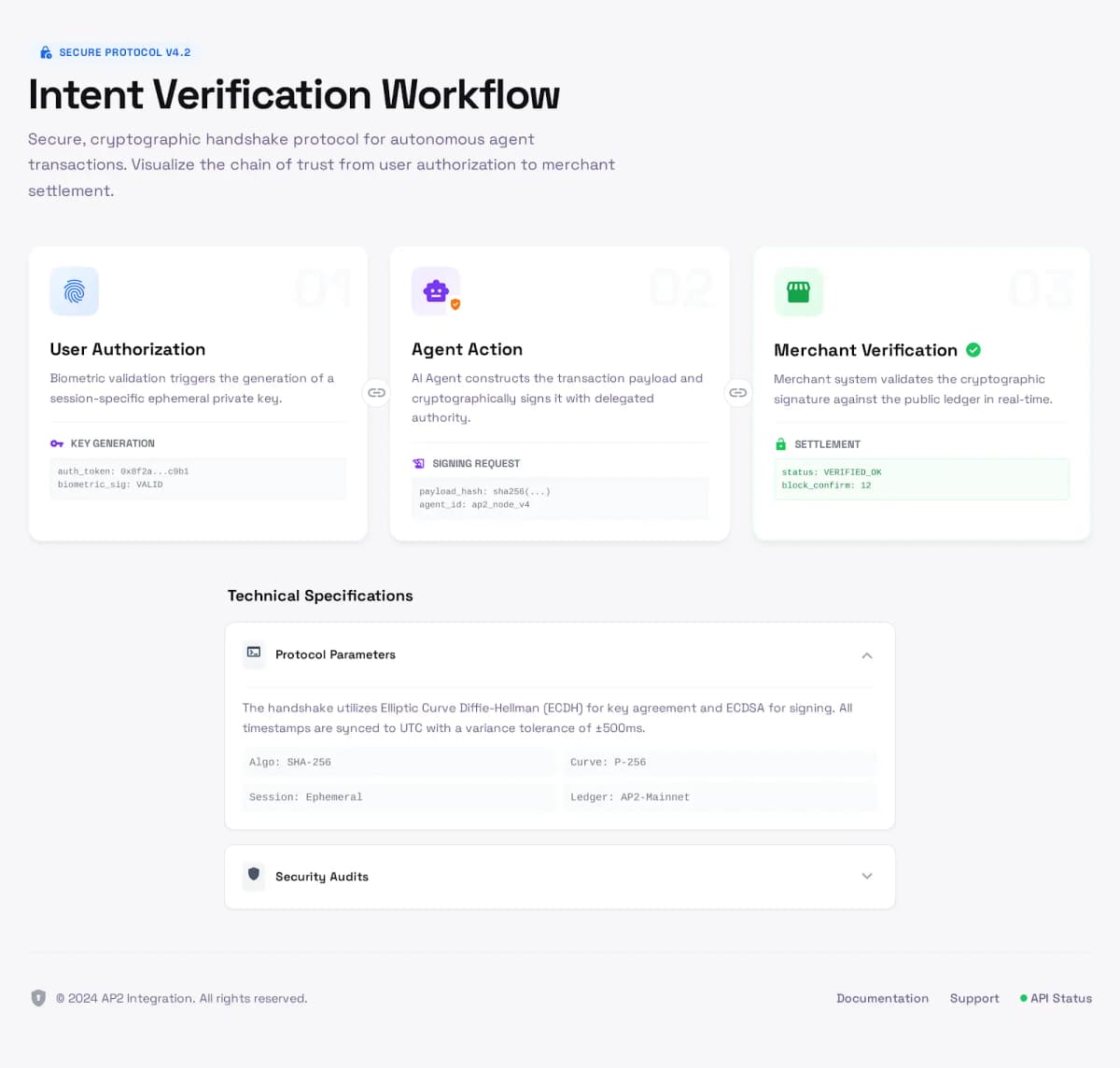
Built for Trust in the AI Era
99.9%
Intent verification accuracy
<100ms
Real-time verification speed
Zero
Hallucination-based fraud
Complete Protection Against AI Agent Risks
Protect your business from the unique challenges of AI-powered commerce. Verify intent, prevent fraud, and build customer trust.
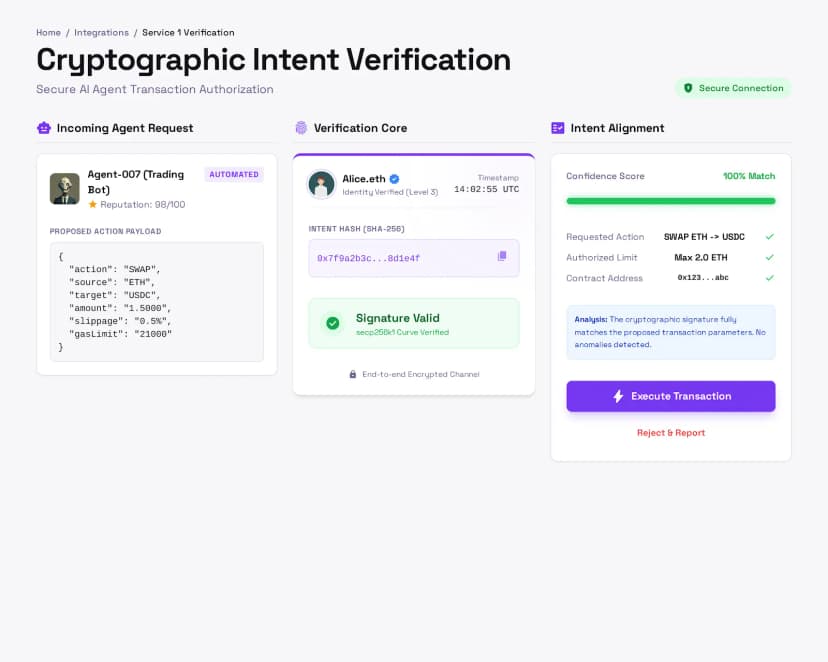
Cryptographic Intent Verification
Every AI agent action is linked to user intent through cryptographic signatures. Verify that requests authentically represent what users actually want, not AI hallucinations or errors.

Cryptographic Intent Verification
Every AI agent action is linked to user intent through cryptographic signatures. Verify that requests authentically represent what users actually want, not AI hallucinations or errors.
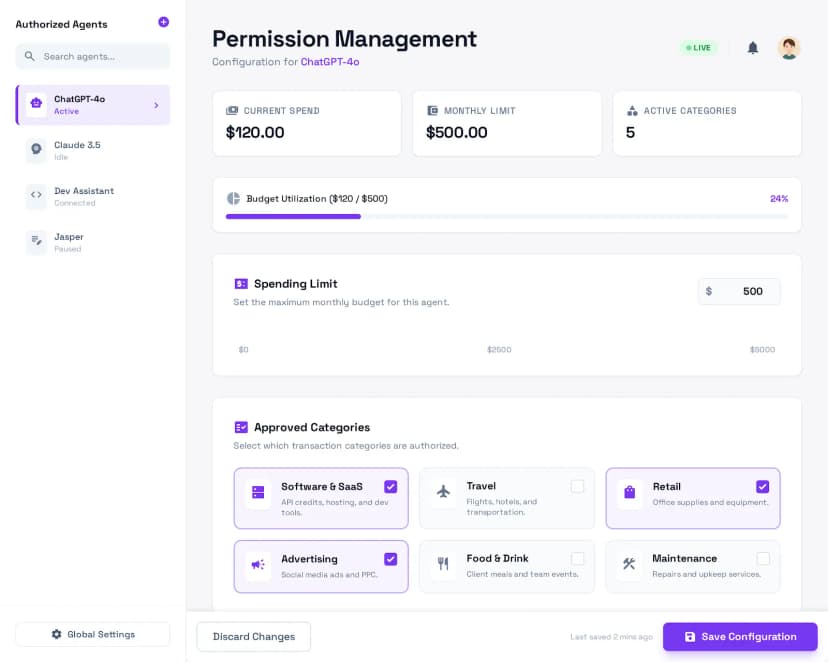
Granular Permission Controls
Users define exactly what their AI agents can do. Set spending limits, approved categories, time windows, and transaction types. Agents can only act within explicitly granted boundaries.
Granular Permission Controls
Users define exactly what their AI agents can do. Set spending limits, approved categories, time windows, and transaction types. Agents can only act within explicitly granted boundaries.

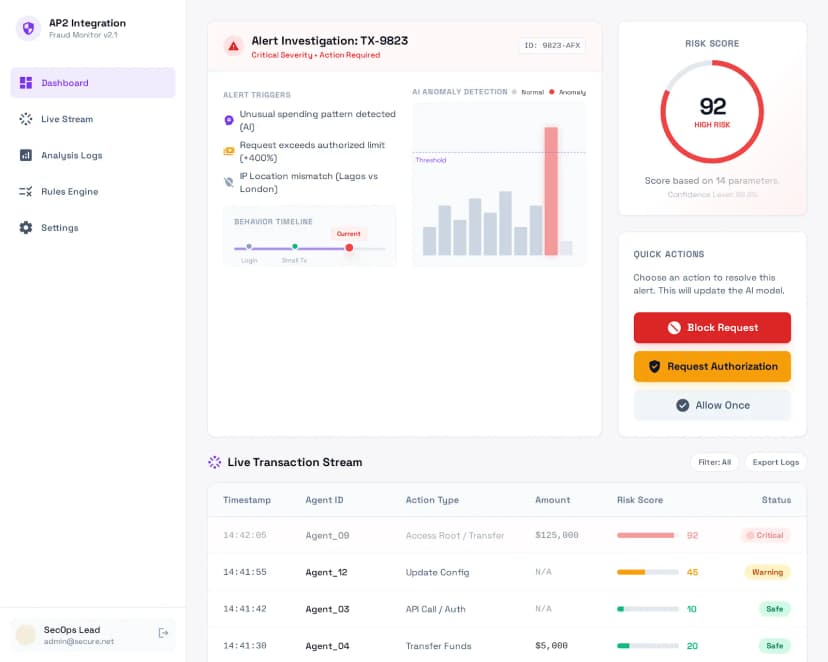
Real-Time Fraud Prevention
Detect and block unauthorized agent actions instantly. Our system identifies anomalies, flagging requests that deviate from user patterns or exceed authorized permissions before processing.

Real-Time Fraud Prevention
Detect and block unauthorized agent actions instantly. Our system identifies anomalies, flagging requests that deviate from user patterns or exceed authorized permissions before processing.
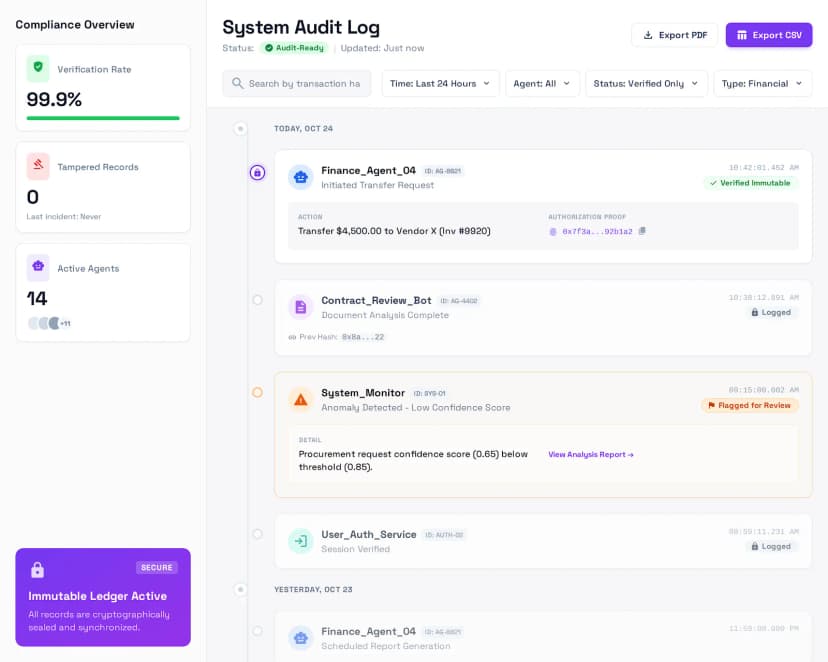
Audit Trail & Compliance
Complete transaction history linking every action to verified user intent. Meet regulatory requirements with immutable records of authorization, execution, and verification for AI-initiated transactions.
Audit Trail & Compliance
Complete transaction history linking every action to verified user intent. Meet regulatory requirements with immutable records of authorization, execution, and verification for AI-initiated transactions.

Compliance
VOVE ID ensures robust security with 24/7 monitoring, strict controls, and a dedicated security team




Why Choose VOVE ID for AI Agent Verification
Leading the industry in AI agent authentication. Get cryptographic intent verification, granular controls, and complete audit trails.
| VOVE ID | Traditional Systems | |
|---|---|---|
| Cryptographic Intent Verification | ✓ Built-in | Not available |
| Real-time Verification Speed | <100ms | N/A |
| Granular Permission Controls | Fully customizable | Basic yes/no |
| Audit Trail & Compliance | Complete immutable records | Basic logs |
| Integration Complexity | Single SDK, <1 day | Multiple systems |
| VOVE ID | Traditional Systems | Basic Auth | Other Providers | |
|---|---|---|---|---|
| Cryptographic Intent Verification | ✓ Built-in | Not available | Not available | Limited, Add-on |
| Real-time Verification Speed | <100ms | N/A | N/A | 2-5 seconds |
| Granular Permission Controls | Fully customizable | Basic yes/no | Basic yes/no | Limited templates |
| Audit Trail & Compliance | Complete immutable records | Basic logs | Basic logs | Partial records |
| Integration Complexity | Single SDK, <1 day | Multiple systems | Multiple systems | Complex, 1-2 weeks |
